Saturday, February 17, 2007
Sunday, December 17, 2006
Running Internet Explorer on Fedora Core 6 Linux
Why would i need an Internet Explorer when there is Firefox?? nah, JobsDB does'nt run on Firefox... so i have to install IE on Linux....
Tuesday, December 12, 2006
Installing SnortAlog with Snort Log Intrusion Detection System Rotation
Installing SnortAlog with Snort Log Rotation
1. Download the latest SnortAlog at http://jeremy.chartier.free.fr/snortalog/downloads/snortalog/
#wget http://jeremy.chartier.free.fr/snortalog/downloads/snortalog/snortalog_v2.4.0.tgz
#tar –xvzf snortalog_v2.4.0.tgz
2. Download and install the Requirements of SnortAlog found at
http://jeremy.chartier.free.fr/snortalog/download.html
3. This is an edited script that I found on the mailing list of Snort. My promiscuous Ethernet card is eth1
snort_log_rotation
| # # Logfile rotation script for snort writen by jameso@elwood.net. # # This script is pretty basic. We start out by setting some vars. # Its job is tho rotate the days logfiles, e-mail you with what # it logged, keep one weeks worth of uncompressed logs, and also # keep compressed tgz files of all the logs. It is made to be run # at midnight everynight. This script expects you to have a base # dir that you keep all of your logs, rule sets etc in. You can # see what sub dirs it expects from looking at the var settings # below. # # Things to note in this script is that we run this script at 12 # every night, so we want to set the dirdate var the day the script # runs minus a day so we label the files with the correct day. We # Then create a dir for the days logs, move the log files into # todays dir. As soon as that is done restart snort so we don't miss # anything. Then delete any logs that are uncompressed and over a # week old. Then compress out todays logs and archive them away, and # end up by mailling out the logs to you. # # Define where you have the base of your snort install #snortbase=/usr/snort snortbase=/var/log/snort # Define other vars # logdir - Where the logs are kept # oldlogs - Where you want the archived .tgz logs kept # weeklogs - This is where you want to keep a weeks worth of log files uncompressed # dirdate - Todays Date in Month - Day - Year format # olddirdate - Todays date in the same format as dirdate, minus a week logdir=$snortbase oldlogs=$snortbase/oldlogs weeklogs=$snortbase/weeklogs # When I first wrote this script, I only ran it on BSD systems. That was a # mistake, as BSD systems have a date command that apperently lets you walk the # date back pretty easily. Well, some systems don't have this feature, so I had # to change the way that dates are done in here. I left in the old way, because # it is cleaner, and I added in a new way that should be portable. If anyone # has any problems, just let me know and I will try to fix it. # # You have to change the system var to either bsd or other. Set it to bsd if # your system supports the "-v" flag. If you are not sure, set it to other. system=other if [ $system = bsd ] then dirdate=`date -v -1d "+%m-%d-%y"` olddirdate=`date -v -8d "+%m-%d-%y"` else [ $system = other ] month=`date "+%m"` yesterday=`expr \`date "+%d"\` - 1` eightday=`expr \`date "+%d"\` - 8` year=`date "+%y"` dirdate=$month-$yesterday-$year olddirdate=$month-$eightday-$year fi # Create the Dir for todays logs. if [ ! -d $weeklogs/$dirdate ] then mkdir $weeklogs/$dirdate fi # Move the log files into todays log dir. This is done with # a for loop right now, because I am afriad that if alot is # logged there may be to many items to move with a "mv *" # type command. There may a better way to do this, but I don't # know it yet. for logitem in `ls $logdir` ; do mv /var/log/snort/$logitem $weeklogs/$dirdate done # Kill and restart snort now that the log files are moved. #kill `cat /var/run/snort_fxp0.pid` pid=`ps -ef | grep 'snort -i eth1' | grep -v grep | awk '{print $2}'` kill -9 $pid # Restart snort in the correct way for you #/usr/local/bin/snort -i fxp0 -d -D -h homeiprange/28 -l /usr/snort/log \ #-c /usr/snort/etc/08292k.rules > /dev/null 2>&1 /usr/local/bin/snort -i eth1 -c /etc/snort/snort.conf -D > /dev/null 2>&1 # Delete any uncompressed log files that over a week old. if [ -d $weeklogs/$olddirdate ] then rm -r $weeklogs/$olddirdate fi # Compress and save the log files to save for as long as you want. # This is done in a sub-shell because we change dirs, and I don't want # to do that within the shell that the script runs in. cd $weeklogs; tar zcvf $oldlogs/$dirdate.tgz $dirdate > /dev/null 2>&1 # Mail out the log files for today. #cat $weeklogs/$dirdate/snort.alert | mail -s "Snort logs" you@domain.com #cat $weeklogs/$dirdate/snort_portscan.log | # mail -s "Snort portscan logs" you@do #main.com |
snortalog_rotation
| month=`date "+%m"` yesterday=`expr \`date "+%d"\` - 1` eightday=`expr \`date "+%d"\` - 8` year=`date "+%y"` dirdate=$month-$yesterday-$year ./snortalog.pl -file /var/log/snort/alert -r -report -o $dirdate.pdf ./snort_log_rotation |
snort_log_rotation and snortalog_rotation script was saved and given an execute permission inside the folder of snortalog. You can play with the other options that has comment on the script.
#./snortalog_rotation << style=""> then it will restart Snort and recreate Snortlog file at /var/log/snort/. Add this on your weekly cronjobs
Monday, December 11, 2006
Linux Professional Institute (LPI) exam prep
Monday, December 04, 2006
Monday, November 27, 2006
List of Spamassassin Rules and RBLs
#cd /etc/mail/spamassassinTo restart spamassassin
#wget http://www.timj.co.uk/linux/bogus-virus-warnings.cf
#wget http://mywebpages.comcast.net/mkettler/sa/antidrug.cf
#wget http://www.emtinc.net/includes/backhair.cf
#wget http://www.timj.co.uk/linux/bogus-virus-warnings.cf
#wget http://www.emtinc.net/includes/chickenpox.cf
#wget http://www.sa-blacklist.stearns.org/sa-blacklist/sa-blacklist.current.uri.cf
#wget http://www.sa-blacklist.stearns.org/sa-blacklist/random.current.cf
#wget http://www.rulesemporium.com/rules/99_FVGT_Tripwire.cf
#wget http://www.nospamtoday.com/download/mime_validate.cf
#wget http://bl.csma.biz/csma.cf
#wget http://www.ahbl.org/docs/mailservers/spamassassin.txt
#/etc/init.d/spamassassin restart
#service spamassassin restart ( in RHEL or CentOS Enterprise Linux system)
SpamAssassin Rules Emporium
http://www.rulesemporium.com/
Testing your Rules
#spamassassin --lint -D
This command will check if there are errors on your Spamassassin rules
Real Time Block List (RBL)
relays.ordb.org
bl.spamcannibal.org
list.dsbl.org
bl.spamcop.net
dnsbl.njabl.org
cbl.abuseat.org
opm.blitzed.org
sbl.spamhaus.org
List updated: Nov 28, 2006
Endian Update
root@kalasag:~ # w
14:52:34 up 6 days, 22:32, 2 users, load average: 0.03, 0.14, 0.16
More info at my QrooniX blog.
Saturday, November 25, 2006
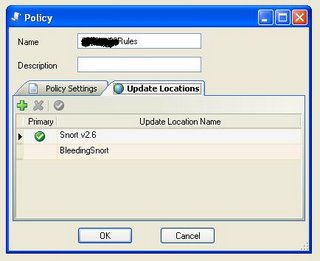
Updating Snort Rules
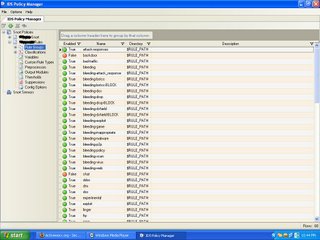
You can use both Snort Oinkmaster Rules and Bleeding Edge Snort Rules